What happens when you go to this site?
The first thing that happens when you type atommiccommits.io into the browser and hit enter is that it resolves the domain name.
How does that happen?
The infrastructure involved in a DNS query
Your computer makes a DNS query, over UDP, to its resolver. That’s the server responsible for resolving the DNS query.
There are 4 types of servers involved in a DNS query.
- DNS recursive resolver: receives queries from client machines. Goes and makes additional queries.
- Root nameserver: contains all top level domains (TLDs) of the internet.
- TLD nameserver: the nameservers for top level domains, e.g.
.com. - Authoritative nameserver: the last stop in the query. The one that finally answers it.
My computer uses Cloudflare’s 1.1.1.1 recursive resolver. Typically, your computer will use the one provided by your ISP. You can override it, like I did (you will not track my DNS queries AT&T!).
Let’s see this in action.
$ dig +trace atomiccommits.ioThis will return the root nameservers, from the recursive resolver (1.1.1.1).
. 512518 IN NS a.root-servers.net.. 512518 IN NS b.root-servers.net.. 512518 IN NS c.root-servers.net.. 512518 IN NS d.root-servers.net.. 512518 IN NS e.root-servers.net.. 512518 IN NS f.root-servers.net.. 512518 IN NS g.root-servers.net.. 512518 IN NS h.root-servers.net.. 512518 IN NS i.root-servers.net.. 512518 IN NS j.root-servers.net.. 512518 IN NS k.root-servers.net.. 512518 IN NS l.root-servers.net.. 512518 IN NS m.root-servers.net.;; Received 525 bytes from 1.1.1.1#53(1.1.1.1) in 41 msOne of those will be used, and then we’ll try to go to a top level domain nameserver.
io. 172800 IN NS a0.nic.io.io. 172800 IN NS a2.nic.io.io. 172800 IN NS b0.nic.io.io. 172800 IN NS c0.nic.io.;; Received 628 bytes from 193.0.14.129#53(k.root-servers.net) in 30 msNow one of these will be used, and we’ll try to get the authoritative nameservers
for atomiccommits.io.
atomiccommits.io. 86400 IN NS carla.ns.cloudflare.com.atomiccommits.io. 86400 IN NS tanner.ns.cloudflare.com.;; Received 602 bytes from 2a01:8840:a1::17#53(a2.nic.io) in 31 msThen we’ll query one of the authoritative nameservers, and get some DNS records in response.
atomiccommits.io. 300 IN A 172.67.201.200atomiccommits.io. 300 IN A 104.21.58.68;; Received 77 bytes from 162.159.44.97#53(tanner.ns.cloudflare.com) in 9 ms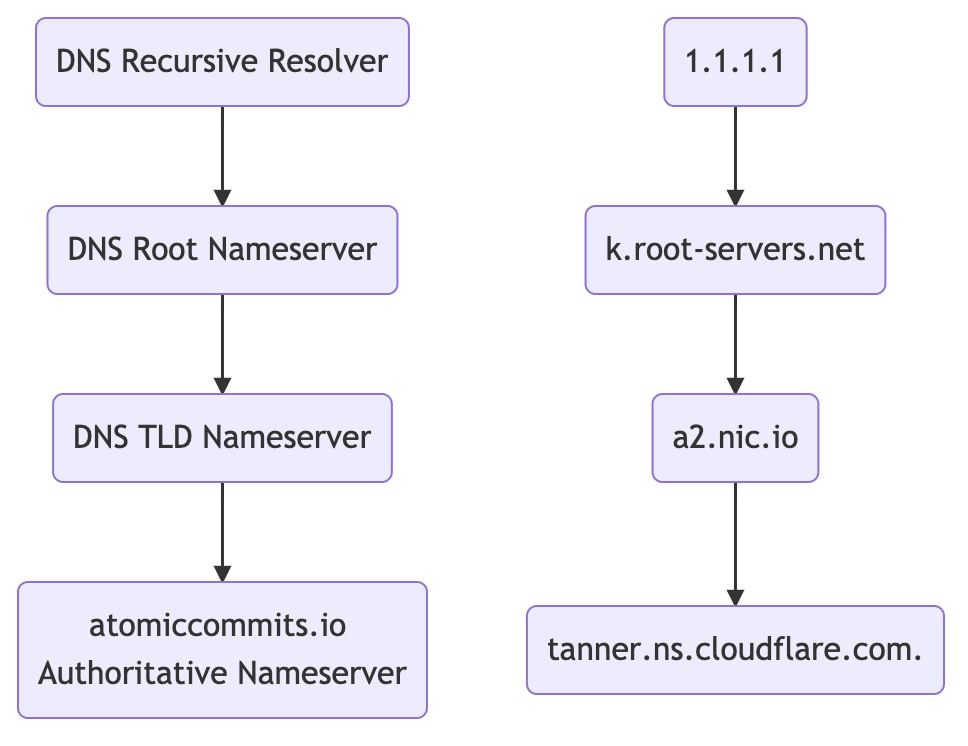
The returned result are these A records.
atomiccommits.io. 300 IN A 172.67.201.200atomiccommits.io. 300 IN A 104.21.58.68DNS Records
There are a lot of different types of DNS records, but just a few we need to know for this.
A recordscontain an IP address for some domain.AAAA recordsare the same, for IPv6. A = address.CNAME recordsforward one domain or subdomain to another.NS recordssay what server is the authoritative nameserver for that domain. For this site, it’stanner.ns.cloudflare.com..
Switching nameservers really just means changing the server and database responsible for answering questions about your domain.
DNS queries ultimately need to arrive at an A record.
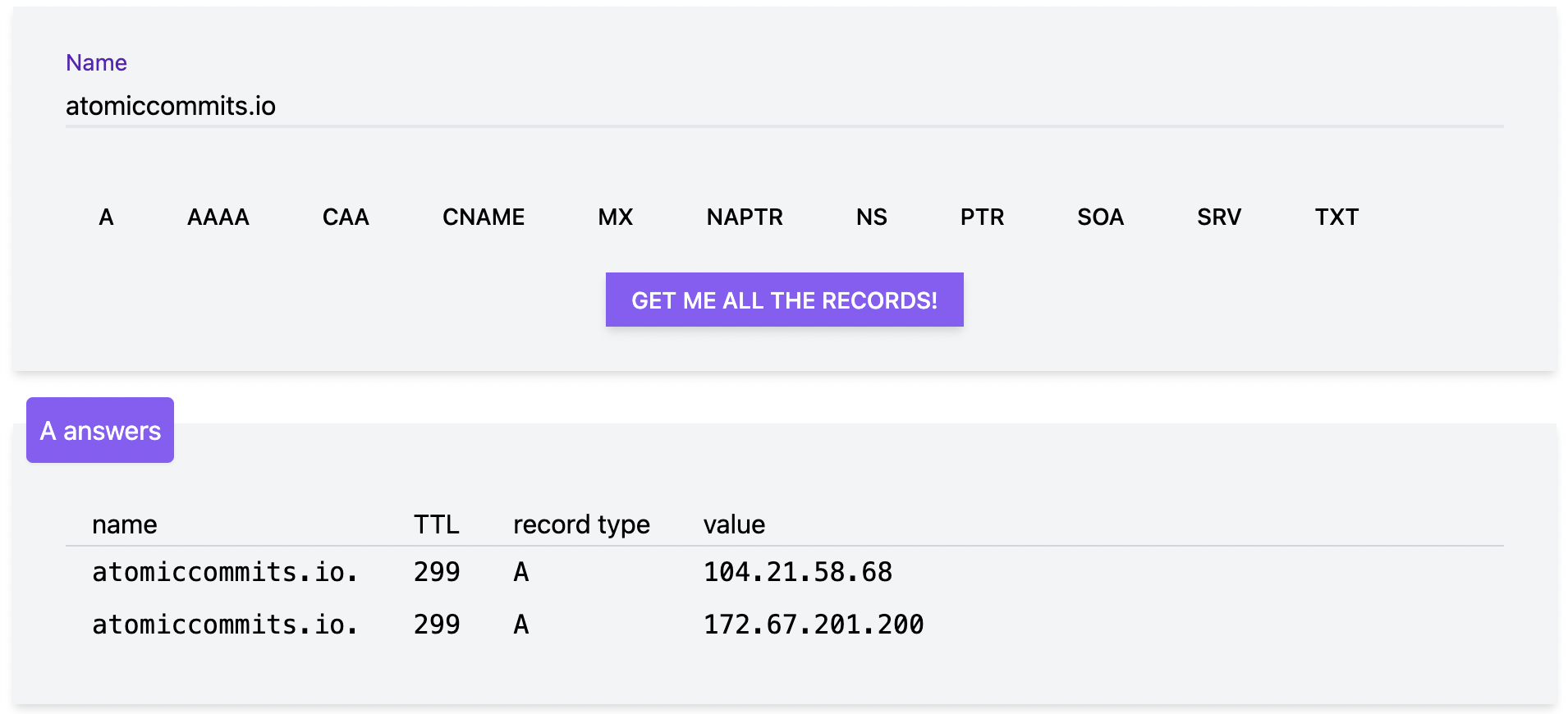
(Screenshot from Julia Evan’s DNS tool.)
One limitation is that you can’t create CNAME records for the apex domain (e.g. atomiccommits.io), whereas it’s fine for a subdomain (e.g. www.atomiccommits.io). Here’s a good explanation of why.
However, Cloudflare an awesome feature called CNAME flattening, where it let’s you create a CNAME record for the root domain, and under the hood it goes and gets the IP for the domain you pointed at and creates an A record.
I use this because I deploy this site to Netlify, and they give me the url condescending-franklin-2dadfd.netlify.app. I want to just redirect atomiccommits.io to that, and a CNAME record is the most natural way to do that.
The IP addresses returned in the above A records are for Cloudflare’s proxy servers.
They proxy to the real IP address, which is a server under Netlify’s control. I do this out of habit — using Cloudflare’s proxying can protect you from DDOS attacks, provide HTTPS if you only have HTTP, and is generally a good security practice.
Additional Thoughts
Overriding domains in /etc/hosts
Sometimes my wife asks me to block Facebook and Instagram on her computer, so she can focus. I don’t like installing extra stuff unnecessarily, so I override their domains in her /etc/hosts file.
When you go to facebook.com, it’s redirecting you to www.facebook.com.
$ curl -IL facebook.comHTTP/1.1 301 Moved PermanentlyLocation: https://facebook.com/# ...
HTTP/2 301location: https://www.facebook.com/# ...
# Finally, when we hit www.facebook.com we get a 200HTTP/2 200# ...That pattern, of having the apex domain redirect to the www subdomain, is common.
So, I make a custom DNS entry in the etc/hosts file for www.facebook.com.
0.0.0.0 www.facebook.comThen she gets this if she tries to go there in the browser.
Note that dig and nslookup ignore your /etc/hosts file. You have to use dscacheutil to verify your change.
$ dscacheutil -q host -a name www.facebook.com
name: www.facebook.comip_address: 0.0.0.0You can use that for normal DNS queries, and also to flush your OS’s DNS cache.
$ dscacheutil -q host -a name alexhwoods.com
name: alexhwoods.comip_address: 76.76.21.21
$ dscacheutil -flushcacheWhat is a DNS Zone?
A zone in the DNS is a distinct area of management.
They can correspond to one domain or several — a zone can contain multiple subdomains.
For example, atomiccommits.io and blog.atomiccommits.io could be in one zone, while shop.atomiccommits.io could be in another.
A DNS zone is really about control, access, and management.
Why does updating DNS records take a while to propagate?
There is caching everywhere in the process of resolving a domain. In your browser. In your OS. In the recursive resolver. Everywhere.
Records have a time to live, which is how long records stay in any particular cache. And since there’s many caches that a record needs to expire in, it gives the appearance of gradual propagation.
After you have an IP, what’s next?
- TLS
- Making the HTTP request, the simplest part
- Rendering HTML, CSS, and JavaScript in your browser
Wow! You read the whole thing. People who make it this far sometimes
want to receive emails when I post something new.
I also have an RSS feed.